Detect to Correct Functions
Description
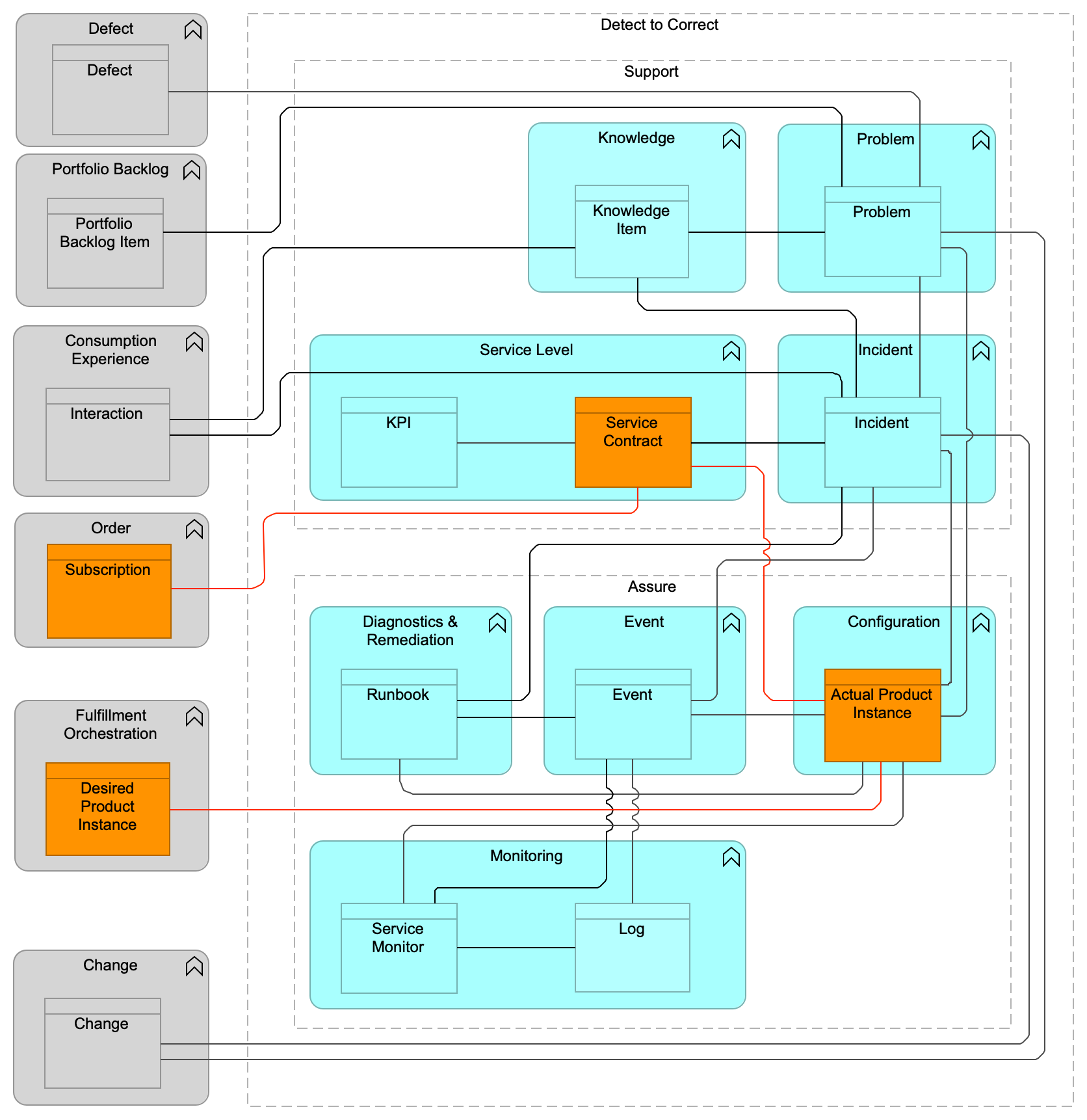
The Detect to Correct functions, informally referred to as “Run”, provide a framework for the operation of Digital Products, supporting the running services and systems while assuring that all running services are operating within stated boundaries and in a secure manner. The Detect to Correct functions also provide a comprehensive overview of the business of digital operations and the services delivered by an Operations team, including security operations. This viewpoint provides an understanding of the inter-relationships among its many domains, and responsiveness to business requests and requirements.
The Detect to Correct functions bring operations functions together to enhance services and efficiencies – thus reducing risk.
The Detect to Correct functions contain the following functional components:
-
Support functions:
-
Incident component
-
Problem component
-
Service Level component
-
Knowledge component
-
-
Assure functions:
-
Monitoring component
-
Event component
-
Configuration component
-
Diagnostics & Remediation component
-
The Detect to Correct functions accommodate the technical inter-relationships and inter-dependencies required to fix operational issues and improve the ability to support business objectives by providing agility, increased uptime, and lower per-service cost.
Related Value Streams
The following value streams use one or more functional components from the Detect to Correct functions:
-
Evaluate
-
Consume
-
Deploy
Business Benefits
The Detect to Correct functions enable organizations to increase efficiency, reduce cost, reduce risk, and drive continuous service improvement by defining the data objects and data flow required to integrate the operations of multiple domains.
The main benefits of using the Detect to Correct functions are:
-
Increase efficiency and reduce cost by:
-
Focusing responses based on causal factor, priority, and business impact
-
Increasing the sharing of information and the reduction of multiple entries of the same data
-
Creating a prescriptive data flow between Event, Incident, Problem, and Change
-
Centralized Event Management for faster analysis
-
Automation between and across business functions
-
Knowledge management and self-service linkage
-
Driving Service Monitoring configuration and predefined Knowledge linked to the Deliver functions
-
Improving the speed at which issues with an Actual Product Instance are identified
-
Driving operating/service level targets
-
Improving the speed at which issues with an Actual Product Instance are proactively identified before the service impact is severe
-
-
Reduce risk by:
-
Sharing consistent data and configuration information between operational silos
-
Prescriptive data flow and data objects
-
Defining business impact
-
Reducing the need for best-guess routing and clannish knowledge
-
Implementing network security to minimize intrusions that cause DoS, viruses, and theft or corruption of data, and to minimize risk exposure
-
Identifying attack signatures that can disrupt operations and affect compliance
-
Clearly defined ownership
-
Increased uptime by reduced Mean Time To Repair (MTTR)
-
Creating a consistent way of managing service level (SLM) definitions, measurements, KPI calculations, and reporting back to the proper Product Manager or Consumer
-
Performing Threat and Vulnerability Assessments (TVAs)
-
Providing an audit trail
-
-
Continuous service improvement:
-
Defined data objects to be shared with Problem Management
-
Using this accumulated Knowledge as input into the Strategy to Portfolio functions
-
Improved management information and decision-making
-
The Detect to Correct functions provide the ability to efficiently manage operations by monitoring key services, correlating and appropriately escalating Events, sharing knowledge, managing (resolving) Incidents and Problems, tracking the Actual Product Instance and its interdependencies, and doing all of that in an automated way. It ensures that functional components used by groups can work together efficiently, through well-defined control points and data objects, to govern and run operations.