Digital Value Methods
| This topic is covered in further depth in Context II, when product management emerges as a fully formalized capability. However, even in the Founder/Individual context the practitioner should have some idea of product positioning and discovery. |
Description
Once context is at least initially understood, there are a number of well-known approaches that can help the practitioner bridge from an understanding of your product context, to an effective vision for building and sustaining a product:
-
Traditional business case analysis
-
Alexander Osterwalder’s Business Model Canvas™
-
Eric Ries' Lean Startup®
The Business Model Canvas and the Lean Startup may seem more suitable for truly entrepreneurial contexts, but there are many practitioners in larger organizations who apply these techniques as well; the thought experiment is “business within a business”; i.e., intrapreneurship [Kanter 1983].
Business Model Canvas
One recent book that has been influential among entrepreneurs is Alex Osterwalder’s Business Model Generation [Osterwalder 2010]. This document is perhaps best known for introducing the concept of the Business Model Canvas, which it defines as: “a shared language for describing, visualizing, assessing, and changing business models”. The Business Model Canvas uses nine major categories to describe the business model:
-
Key Partners
-
Key Activities
-
Value Proposition
-
Customer Relationships
-
Customer Segments
-
Key Resources
-
Channels
-
Cost Structure
-
Revenue Streams
and suggests they be visualized as in Business Model Canvas (similar to Osterwalder 2010).
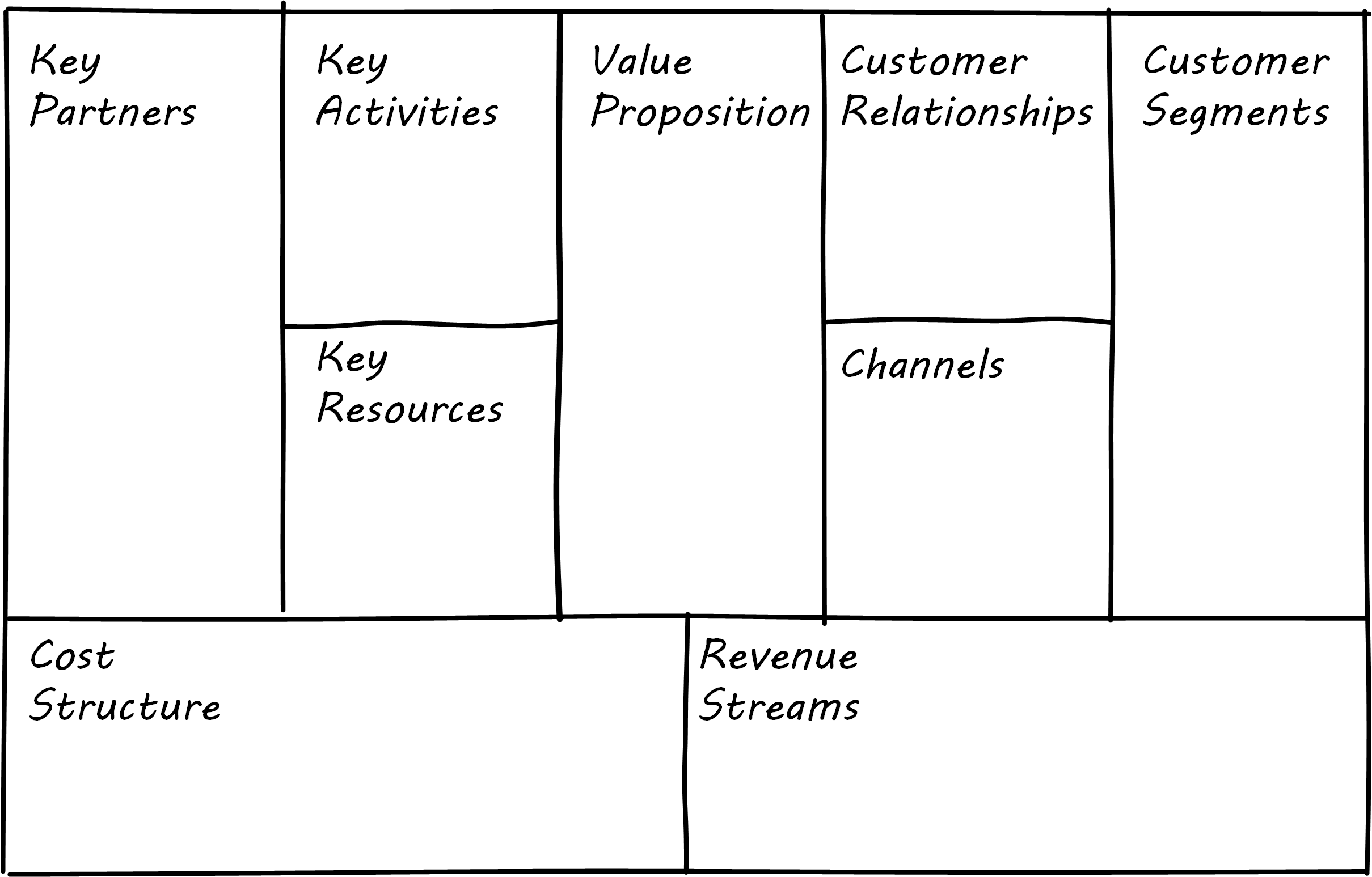
The canvas is then used in collaborative planning; e.g., as a large format wall poster where the business team can brainstorm, discuss, and fill in the boxes (e.g., what is the main “Value Proposition"? Mobile bank account access?).
Osterwalder and his colleagues, in Business Model Generation and the follow-up Value Proposition Design [Osterwalder 2014], suggest a wide variety of imaginative and creative approaches to developing business models and value propositions, in terms of patterns, processes, design approaches, and overall strategy.
Business Case Analysis
There are a wide variety of analysis techniques for making a business case at a more detailed level. Donald Reifer, in Making the Software Business Case [Reifer 2002], lists:
-
Breakeven analysis
-
Cause-and-Effect analysis
-
Cost/Benefit analysis
-
Value Chain analysis
-
Investment Opportunity analysis
-
Pareto analysis
-
Payback analysis
-
Sensitivity analysis
-
Trend analysis
Empirical, experimental approaches are essential to digital management. Any analysis, carried to an extreme without a sound basis in real data, risks becoming a “castle in the air”. But when real money is on the line (even the opportunity costs of the time you are spending on your startup), it is advisable to look at the decision from various perspectives. These techniques can be useful for that purpose. However, once you have some indication there might be business value in a given idea, applying Lean Startup techniques may be more valuable than continuing to analyze.
Lean Startup
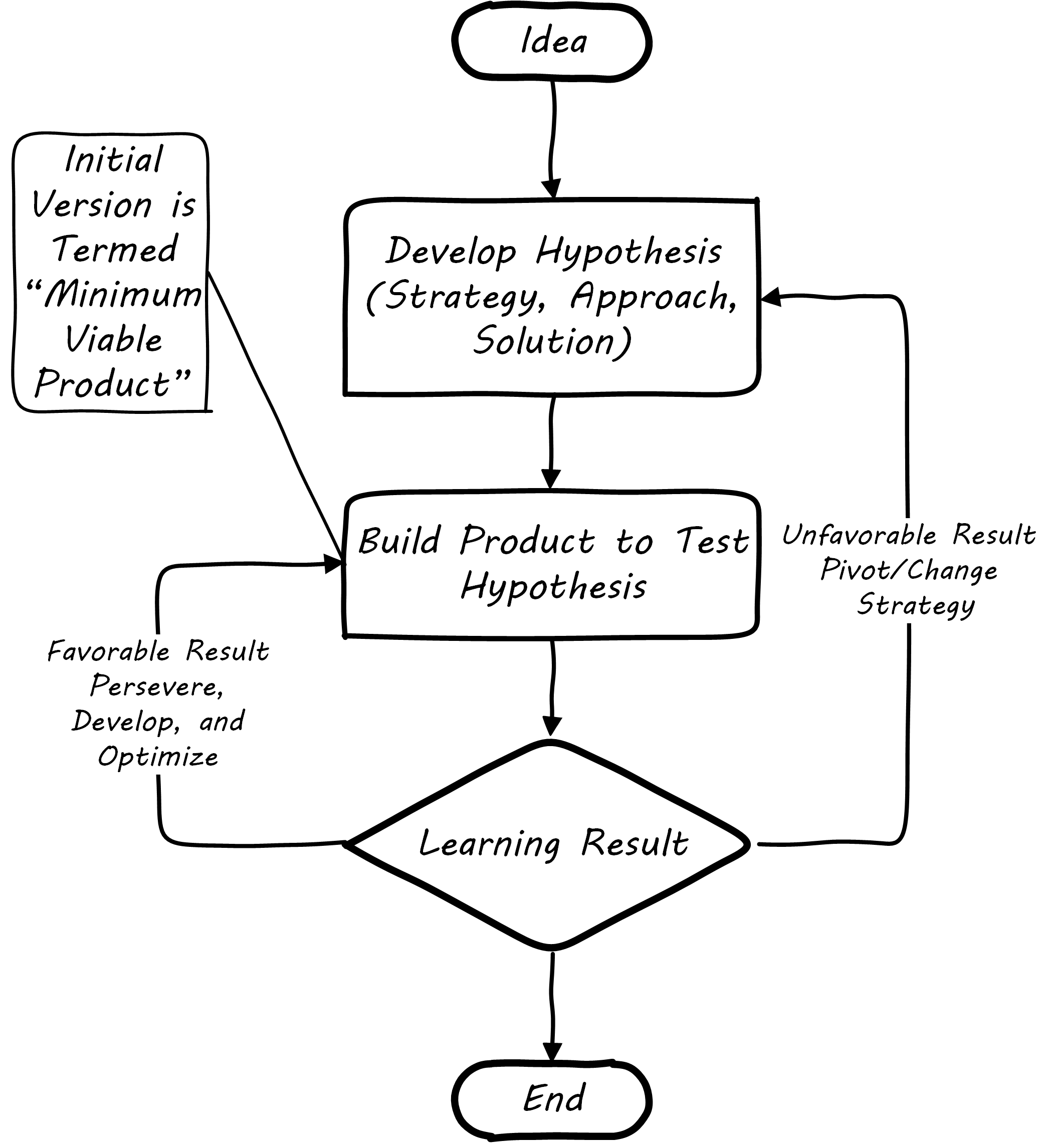
Lean Startup is a philosophy of entrepreneurship developed by Eric Ries [Ries 2011]. It is not specific to IT; rather, it is broadly applicable to all attempts to understand a product and its market. (According to our definition of product management a workable market position is essential to any product.)
The idea of Lean Startup has had a profound influence on product design, including market-facing and even internal IT systems. It is grounded in Agile concepts such as: “Do the simplest thing that could possibly work.”
Lean Startup calls for an iterative, “Build-Measure-Learn” cycle; see Lean Startup Flowchart, a summary of ideas from Ries 2011. Repeating this cycle frequently is the essential process of building a successful startup (whatever the digital proportion):
-
Develop an idea for an MVP
-
Measure its effectiveness in the market (internal/external)
-
Learn from the experiment
-
Decide to persevere or pivot (change direction while leveraging momentum)
-
New idea development, evolution of the MVP
Flowcharts such as Lean Startup Flowchart are often seen to describe the Lean Startup process.
Digital Security
A Digital Practitioner often starts by thinking about value creation through their digital products or services. However, now is also the time to think about protecting that digital value. Your customers will be sharing data about themselves, their preferences, and even financial information; e.g., credit cards to make purchases. Failure to protect that data can irreparably damage any other digital value you manage to create; it will certainly damage your or your organization’s reputation, and may have financial consequences.
Architects of buildings need to appreciate that the physical materials that will implement their creations need to be strong enough to produce the envisioned construct. Similarly, a Digital Practitioner needs to understand that software can be weak and they need to appreciate how to examine the software artifacts for the precursors of those weaknesses that would threaten the operational capabilities and integrity of their envisioned constructs.
Attack surface analysis, design reviews for security weaknesses, static source code analysis for weaknesses, dynamic fuzz testing, adversary-based pen testing, and binary analysis are all techniques used to gain confidence that dangerous failure modes of the software-based system are not rampant, and that some evidence-based argument can be made about the adequacy of the rigor used to create the software.
In the building of buildings, this is done by the engineering elements of a team, along with building code inspectors and material scientists, but the analogous activities are not the norm in software systems. So, as you go through both the analysis and description phase and the construction phase, keep in mind that that all software has strengths and weaknesses and needs to be checked for weaknesses that would impact the intended functionality, reasoning, and logic. See the Common Weakness Enumeration (CWE) (MITRE®) for examples of weaknesses with security, performance, reliability, and maintainability consequences.
As software-enabled elements become more entwined in our physical lives, whether at work or not, there needs to be attention paid to this line of thinking in the education of the software-based systems work force.
A deeper treatment of this subject can be found in the later chapter on Security and in The TOGAF® Series Guide: Integrating Risk and Security Within a TOGAF® Enterprise Architecture [G152].
Evidence of Notability
The complex process of discovering and supporting digital value is covered in industry work on Digital Transformation (Westerman 2014 and W17D). It is also addressed as an important sub-topic within the product management literature, especially at its intersection with Agile. Product management is a large and growing professional community, with a major professional organization (the Product Development and Marketing Association) and many less formalized meetings and groups. It has a correspondingly rich body of professional literature (Blank 2013, Cagan 2018, and Gothelf & Seiden 2013). Product management is also a major topic at Agile conferences.
Limitations
Some digital efforts are more instrumental, and provide value in the same way that a cog provides value to a machine. They have little independence. Discussions of value imply greater autonomy to act on the analysis. Business case analysis would rarely be applied in the engineering of a small component; similarly, business case analysis makes less sense with digital systems whose existence is required by a larger whole. It is at the level of that larger whole that value analysis should take place.
Related Topics